
News


The Advantages of Microsoft 365 Copilot

Why EDR Matters More Than Ever
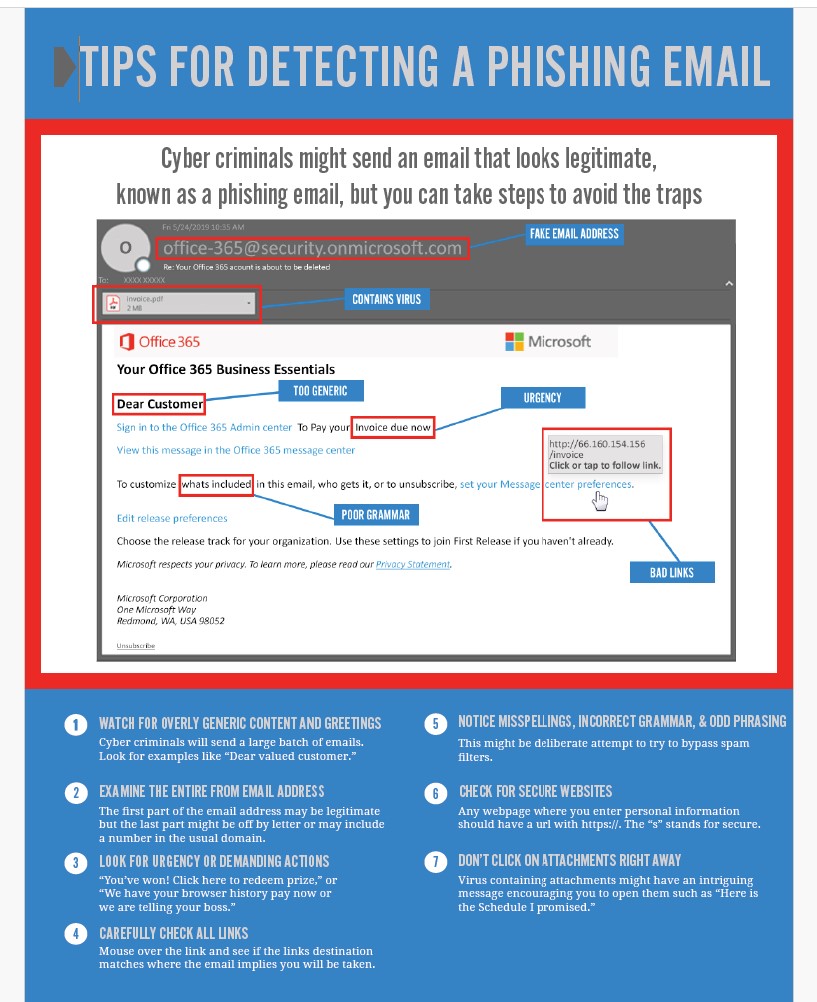
How to spot a Phishing Email

The Importance of Secure IT Defences Against Cyber Criminals

The Crucial Role of Dark Web Monitoring for Stolen Company Login Credentials

Guardians of the Endpoint: The Crucial Role of EDR in Modern IT Security




